"DMZ" that can be roughly understood in 5 minutes, easy explanation of roles and construction methods | Business + IT
Solving business issues by integrating IT and management
What is Business + IT?
Login
E-mail newsletter registration
What is Business + IT?
Related genres
"DMZ" that can be roughly understood in 5 minutes, gently explains the role and construction method
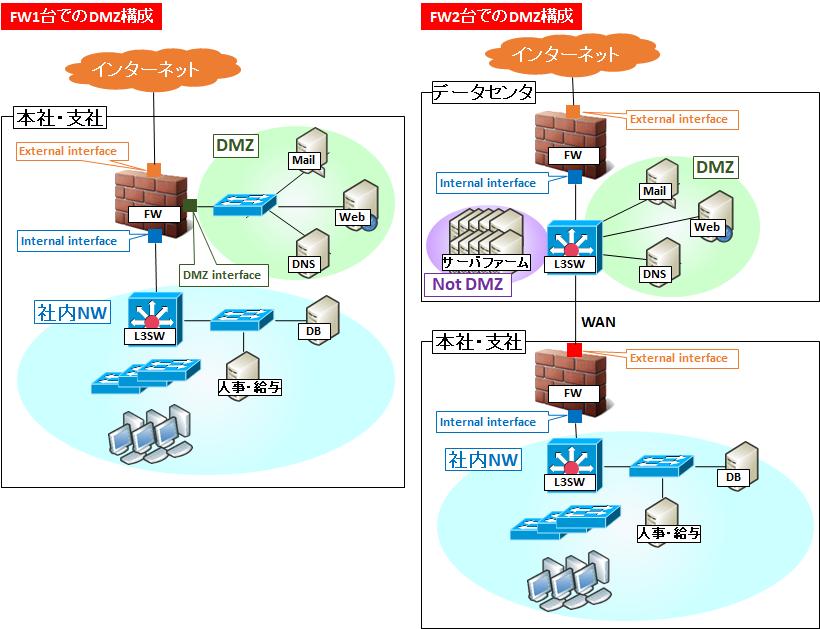
In the world of network security, a special network area called "DMZ" may be created. This acts as a "buffer area" to protect important information and terminals connected to the network. How can a DMZ be built, what features it has, and how it will be used. I will explain the basic mechanism of the DMZ gently.
Freelance writer Naoki Mitsumura
Freelance writer Naoki Mitsumura
Representative of GK Noteip. Writer. He majored in computer science at a university in the United States, and after graduating, engaged in planning and marketing of IT-related products at some listed companies in Japan. After retiring, he has been involved in writing books and articles and creating web content as a writer. In addition to artificial intelligence, he deals with topics related to science, IT, military, and medical care, and also conducts research support activities at research institutes and universities. His books include "Core Technology in the Near Future (Shoeisha)", "Illustration: An Introduction to AI Business (Narumi-do)", and "Artificial Intelligence in Manga (Ikeda Bookstore)".