Why does the attack slip through?
In recent years, the importance of cyber security measures has been shouted loudly, and why is the damage of cyber attacks still reduced despite the fact that many companies are investing a large budget and strengthening measures?
In short, the attacker understands that the defenders are strengthening countermeasures and developing new countermeasures, and the attackers devise more tricks every day.In other words, the endless "plague" has been repeated endlessly, and today's cyber attack uses that hand to pass through existing security measures.
Attack tricks that skillfully slip through existing security measures
I would like to introduce the most commonly used tricks to pass through existing security measures in four types: "deceit", "back", "fake", and "silent".
Deceive (deceive people)
The attacker uses a variety of "deceived techniques" to infect the attack target into malware.For example, in order to open the fraudulent files attached to the phishing email, you will send an e -mail such as a job applicant for a company recruitment person, or an e -mail such as "I attached a file of the payment invoice".Is often used.
There is also a method of abusing the information of the e -mail stolen by the advance attack and sending it to the email that has been exchanged so far to open the attached file.
In the infection method through files, the Microsoft Office macro function is often abused.Therefore, in recent standard settings, security warnings are displayed when a file using a macro function is opened.Therefore, the attacker sides the user to enable the macro by displaying a message such as "If the image is not displayed, click the button for enabling content".To do.
Back (invading from unprecedented areas)
Even if you intend to introduce security software to all PCs and servers in the company, you will be able to take a thorough countermeasure, but if there is a little omission or leakage behind the scenes, it will allow malware to enter.
For example, terminals, cloud services, terminals for overseas bases, and terminals that are newly added by the business department, terminals for overseas bases, and other terminals, are likely to be leaked from the IT department management target.The attacker finds the vulnerabilities caused by the omissions and leakage of such management, and by throwing it, it invades from the "back door".
False (it will be a regular user or a regular program)
There are many ways to use the ID / password information that have been leaked in the past to become a regular user and attack.In recent years, it has become common to use regular tools that are standard on Windows OS to perform attacks as if it were a regular program processing.
Furthermore, set the file name of the malware to the same as the regular program, add the stolen regular signature to the file, and put the malware file as if it were a regular program file.It is also used as a matter of course.
In addition, there are many tricks to exploit tools and services used in the company's regular business, such as remote access tools.In such a regular user or a process, the attacks performed, making it difficult to distinguish from the regular processing, making it easier to detect detection.
Silent (hide so that it is not detected)
Some security products today are to first execute suspicious files in a safe area to observe and analyze their behavior to determine whether they are malware.This allows you to effectively detect unknown attacks that cannot be detected by antivirus software pattern matching.
However, some malware judge whether the environment in which you are running is an analysis environment of a security product, and if it is so, it is programmed to avoid the detection to escape.。Also, as a simple method, it does not work immediately after entering, and some are started for the first time after a certain period of time.
Why is the cyber attack method becoming more and more sophisticated?
In addition to the above, today's cyber attacks will make full use of that hand to pass through the defense side measures.Therefore, the attacker needs to check the latest information every day and continue to develop new methods.
Until the effort and cost of that, the attacker pours heart blood to the advanced and sophisticated tricks, because it has already been established as a business where cyber attacks can be expected to make a big reward.yeah.
According to Cyber Security Ventures, a cyber security research company, cyber crimes were 6 trillion in 2021 and 10 in 2025..It is said to reach 5 trillion yen.Japan's 2020 annual GDP is about $ 5 trillion, so the amount of cyber crimes has already exceeded this.
If it is much less likely to be arrested compared to the real world crimes, it will be incentive for the attacker as a full -fledged crime business.
Therefore, we will recruit and organize the personnel extensively, and collect information on new vulnerabilities and attack methods.In this way, we develop and try new attack methods every day, and if fail, we will analyze the cause and make improvements.As long as the attacker continues to turn this process, the plague with the defense will never end.
Attack methods that are difficult to detect in old -fashioned security measures
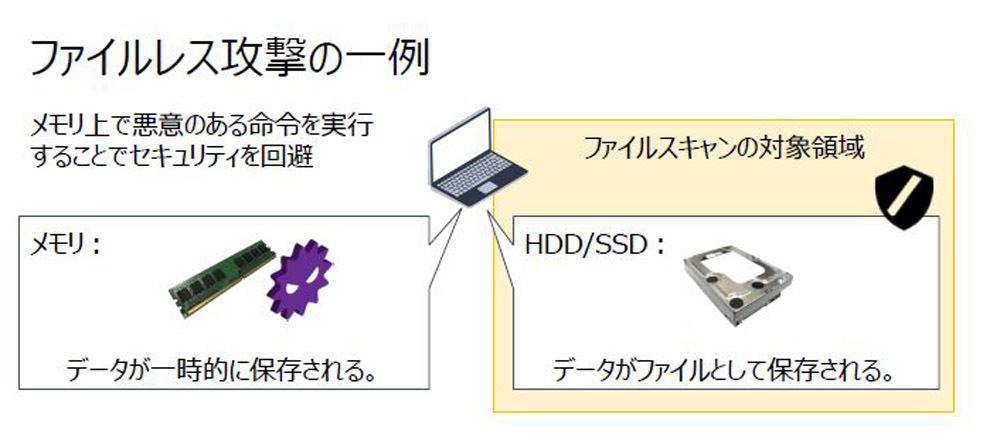
One of the representatives of the attack method that can through traditional security measures is "fileless attack".As the name implies, this is a method of launching an attack, such as having an unauthorized order on a memory where the data is temporarily recorded without having an entity as a file.Since traditional virus software is conducted on files, we are aiming for a gap that malware that does not exist as a file cannot be detected.
In addition, malware, which was deployed in the memory and executed an attack, becomes more difficult to detect and analyze subsequent analysis because the traces disappear from the memory when the terminal is shut down.
Among fileless attacks, it is difficult to detect a method called "environment parasitic attack", which abuses "Lolbin (Living Off the Land Binari)", with traditional security measures.This is a trick that exploits standard tools and commands of Windows OS such as "PowerShell" and "WMI" to attack, and the files to be investigated become a regular tool, and at first glance, it's a regular tool.It is difficult to detect because it cannot be distinguished from the processing of.
Furthermore, it is difficult to prevent the "zero -day attack" that launches an attack from the announcement of the vulnerability of the OS and application to the revision program.It is an advantage for the attacker until the vulnerability is published and the company takes that countermeasures.
What measures should be taken?
So, what kind of work should we take to attack existing security measures using various hands in this way?
The first thing to keep in mind is to gather information about new threats and its countermeasures.As already mentioned, the attacker is constantly collecting the latest vulnerabilities and is busy developing new tricks.In order to compete with this, the defenders must always keep an eye on the latest information and operate the process and system that continues to improve measures without worrying about the introduction of measures.I have.
Another important initiative is to know the "normal condition" of your system and network in advance.As already explained, recent cyber attacks have abused OS tools, so what services and programs are running in normal times, what kind of tools are allowed and prohibited, and them.If you know what kind of communication you are doing, you will be able to quickly detect the attack due to the difference from the tendency of normal time when the malware enters into a regular user or process.
Specifically, it is important to have a system that allows you to collect and analyze various logs from normal times.For example, if you collect Windows audit logs on a regular basis, you will be able to detect attacks by analyzing logs even if you are attacked by PowerShell.
As I say many times, cyber attacks continue to be sophisticated and sophisticated, and slip through various security walls.In order to minimize attacks, you will need to look at the latest trends and your system.
Sawamura intelligence
さわむら とものりCyber Liezen Japan Co., Ltd. Senior Security Advisor
警察庁にてデジタルフォレンジックやサイバー攻撃対策の業務に10年従事した後、サイバーリーズン・ジャパン株式会社に入社。 現在は、サイバー攻撃や脅威情報のリサーチ、サイバーセキュリティ管理体制の高度化に係る教育や支援などを担当。これまでに、大手製造業などの多数のインシデント対応に携わっている。この著者の記事一覧はこちら